Implementing an IT Security Policy Checklist in Google Sheets is an effective strategy for organizations aiming to maintain robust cybersecurity measures. Google Sheets offers a flexible and collaborative platform to design a checklist that tracks essential IT security policies, facilitating data-driven decision-making and operational efficiency.
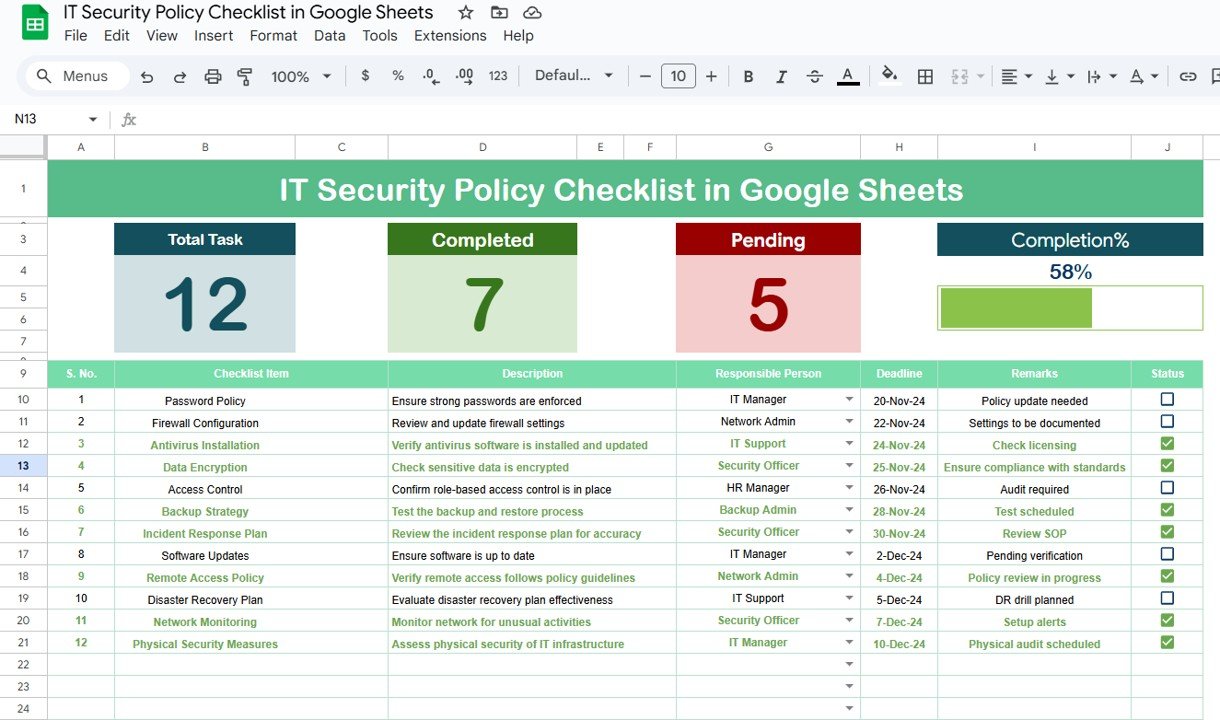
Key Features of the IT Security Policy Checklist in Google Sheets
-
Comprehensive Checklist Overview
-
Structured Task Management: The checklist is organized into sections, each focusing on critical aspects of IT security, such as data protection, network security, and user access controls.
-
Task Assignment and Tracking: Assign tasks to responsible individuals, set deadlines, and monitor the status of each task to ensure timely completion.
-
-
Detailed Task Analysis
-
Task Descriptions and Guidelines: Each task includes a brief description and specific guidelines to ensure clarity and consistency in implementation.
-
Status Indicators: Utilize status indicators to track the progress of each task, facilitating effective monitoring and management.
-
-
Data Management and Customization
-
Dynamic Data Entry: Easily input and update task details, ensuring that the checklist reflects the most current information.
-
Customizable Features: Modify the checklist to align with your organization’s specific IT security policies, adapting to evolving security requirements.
-
-
User-Friendly Navigation and Support
-
Intuitive Interface: Designed for ease of use, the checklist allows users to navigate and manage tasks efficiently.
-
Guidelines and Instructions: Access embedded guidelines and instructions within the checklist to assist users in effectively managing IT security tasks.
-
Benefits of Using the IT Security Policy Checklist in Google Sheets
-
Enhanced Security Compliance: By systematically tracking and managing IT security tasks, the checklist helps ensure adherence to security policies and standards.
-
Improved Operational Efficiency: Identifying and addressing security tasks proactively reduces vulnerabilities and enhances overall security posture.
-
Customization and Flexibility: The checklist can be tailored to meet the unique security needs of your organization, adapting to changing security landscapes.
Getting Started with Your IT Security Policy Checklist in Google Sheets
-
Define IT Security Policies: Identify the key security policies relevant to your organization, such as data encryption, network monitoring, and access controls.
-
Set Up the Checklist: Utilize the provided template or design a customized checklist that includes sections for task descriptions, assignments, deadlines, and status tracking.
-
Input Data: Enter task details, assign responsibilities, and set deadlines to provide a clear roadmap for security policy implementation.
-
Customize Features: Adjust the checklist to reflect your organization’s specific security objectives, including modifying tasks, setting priorities, and personalizing visual elements.
-
Monitor and Update: Regularly review and update the checklist to ensure it reflects current security tasks and aligns with evolving security strategies.
By implementing the IT Security Policy Checklist in Google Sheets, your organization can streamline security policy management, enhance compliance, and make data-driven decisions to improve overall cybersecurity posture.
Click here to read the Detailed blog post
IT Security Policy Checklist in Google Sheets
Visit our YouTube channel to learn step-by-step video tutorials
YouTube.com/@PKAnExcelExpert




























Reviews
There are no reviews yet.