Cyber threats are evolving—your monitoring tools should too. The Cybersecurity Monitoring Checklist in Excel is a simple, smart, and scalable solution designed to help you keep your cybersecurity protocols on track. Whether you manage a small business or an enterprise IT department, this ready-to-use Excel checklist offers a comprehensive system for managing tasks, ensuring compliance, and maintaining accountability across teams.
No complex software, no steep learning curve—just a clean, functional, and fully editable Excel template that puts you in control of your cybersecurity to-do list.
✨ Key Features of Cybersecurity Monitoring Checklist in Excel
📌 Visual Progress Tracker
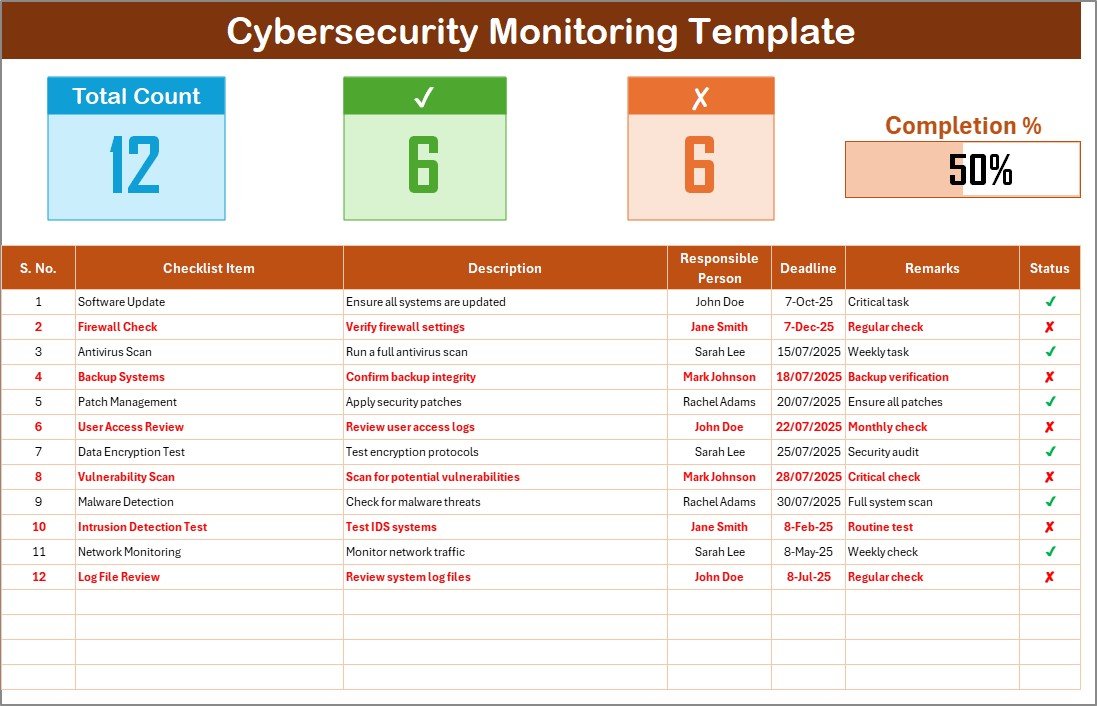
Track your total tasks, completed, and incomplete ones with auto-calculated counts and a dynamic progress bar for visual tracking.
✅ Status Control Using ✔ and ✘
Quickly mark tasks as complete (✔) or not complete (✘) with dropdowns for better visual clarity and reporting.
👤 Role-Based Assignment
Assign each task to a responsible person via an interactive dropdown list, reducing confusion and miscommunication.
📅 Deadline & Remarks Columns
Stay deadline-aware and document important notes for each cybersecurity task to ensure timely execution.
📄 Task Breakdown Table
A structured table captures each task’s Serial No., Checklist Item, Description, Responsible Person, Deadline, Remarks, and Status.
🔄 Auto Summary Panel
Monitor key stats such as Total Count, Checked Count, and Crossed Count at the top of the sheet—automatically updated.
📂 What’s Inside the Cybersecurity Monitoring Checklist?
The template includes two streamlined worksheet tabs:
1️⃣ Cybersecurity Monitoring Checklist Sheet
This is the main action area. You’ll manage tasks, monitor progress, and control status for every cybersecurity-related activity. It features:
-
Status summary (Total, Checked, Crossed)
-
Progress bar
-
Full checklist table with dropdowns and deadline controls
2️⃣ List Sheet
This sheet maintains a dropdown list of Responsible Persons, ensuring consistency and ease when assigning tasks in the main sheet.
🛠️ How to Use the Cybersecurity Monitoring Checklist
-
📥 Download and open the Excel template
-
🧾 Add your cybersecurity tasks to the checklist table
-
👤 Select the responsible person using the dropdown
-
🗓️ Set a deadline and add remarks
-
✔ Update the task status as it progresses
-
🔍 Monitor progress via the summary panel and bar
With built-in conditional formatting and dropdown controls, it’s plug-and-play for anyone familiar with Excel.
👥 Who Can Benefit from This Checklist?
-
🛡️ IT & Cybersecurity Teams – Track updates, audits, and mitigation plans
-
🧑💼 Compliance Officers – Ensure regulatory cybersecurity compliance
-
🏢 SMEs – Establish a basic, effective monitoring structure
-
🧑💻 Managed Security Providers (MSPs) – Use across multiple clients
-
📊 Project Managers – Ensure tasks are completed on time and documented
🔗 Click here to read the Detailed blog post
🔗 Visit our YouTube channel to learn step-by-step video tutorials






























Reviews
There are no reviews yet.