In today’s digital landscape, IT security is a top priority for organizations of all sizes. The IT Security Policy Checklist Template in Excel is a powerful, structured, and easy-to-use tool designed to help IT teams systematically manage security protocols, track compliance, identify gaps, and ensure best practices are followed.
This fully editable and customizable Excel template enables businesses to monitor critical security tasks, enforce cybersecurity policies, and maintain robust IT security measures efficiently.
Why Choose This IT Security Policy Checklist?

With increasing cyber threats, businesses need a structured approach to security management. This checklist helps IT teams and security professionals maintain compliance, streamline security policies, and track implementation progress effectively.
- 📊 Comprehensive Dashboard – Get a quick overview of IT security measures.
- ✅ Task Tracking System – Stay on top of every security task and deadline.
- 🔄 Fully Editable Excel Template – Customize as per organizational needs.
- 🎯 Improve Compliance – Meet industry standards and best practices.
- 🔐 Enhance Security Governance – Identify and eliminate potential risks.
Key Features of the IT Security Policy Checklist Template
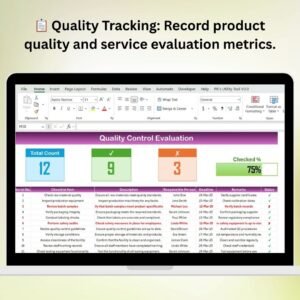
1. IT Security Policy Checklist Tab
The main tracking sheet where all security tasks are documented and monitored.
🔹 Key Metrics at a Glance
- Total Count: Displays all checklist items.
- Checked Count: Tracks completed security tasks.
- Crossed Count: Shows pending security items.
- Progress Bar: Provides a visual indication of task completion.
🔹 Detailed Checklist Table
- Serial No.: Unique identifier for each security task.
- Checklist Item: Title of the security measure.
- Description: Clear details about the security policy or process.
- Responsible Person: Who is in charge of implementing the task.
- Deadline: Expected completion date of the task.
- Remarks: Additional notes or status updates.
- Status: Done ✅ or Pending ❌, making progress tracking effortless.
2. List Sheet Tab
A dedicated sheet to maintain a list of responsible personnel for security tasks.
- This helps in assigning IT security responsibilities efficiently.
- Ensures structured tracking of security compliance.
- Enables the creation of drop-down menus for quick task allocation.
How This Template Helps Your Business
✔ Enhances IT Security Oversight – Monitor and prioritize critical tasks.
✔ Ensures Policy Compliance – Helps meet ISO 27001, NIST, GDPR, and SOC 2 security frameworks.
✔ Reduces Risk Exposure – Prevent security breaches, data leaks, and cyber threats.
✔ Improves Team Coordination – Assign responsibilities clearly.
✔ Boosts IT Governance – Create audit-ready security policies.
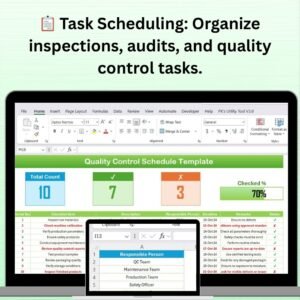
How to Use the IT Security Policy Checklist Template?
Step 1: Input Your Security Tasks
List down all relevant IT security measures, including password policies, firewall configurations, and encryption standards.
Step 2: Assign Responsibilities
Using the List Sheet Tab, assign each security task to a responsible team member.
Step 3: Track Progress
Monitor task completion status with visual indicators and a progress bar.
Step 4: Review & Update
Regularly update security measures, ensuring compliance with evolving security frameworks.
Who Can Benefit from This Template?
💼 IT Managers – Track and implement cybersecurity measures.
📊 Compliance Officers – Ensure industry-standard security compliance.
🔐 Cybersecurity Professionals – Monitor network, system, and data security.
🏢 Businesses & Enterprises – Improve corporate IT security governance.
What’s Included in the Template?
📂 Fully Editable Excel File
📊 Interactive Security Checklist
🔄 Drop-Down List for Task Assignments
📈 Progress Tracking Dashboard
✅ Easy-to-Use Layout & Instructions
Take Control of Your IT Security Now!
Don’t wait for a security breach! Ensure your business stays protected with our IT Security Policy Checklist Template in Excel.
🔹 Instant Download – Get started right away!
🔹 No Coding Required – Simple Excel-based tool.
🔹 One-Time Purchase – Unlimited use.
Click hare to read the Detailed blog post
Visit our YouTube channel to learn step-by-step video tutorials


























Reviews
There are no reviews yet.