Cyber threats, data breaches, and unauthorized access are risks that no business can afford to ignore. From small organizations to global enterprises, IT Security To-Do List Checklist has become a top priority. Yet, without a structured system, critical tasks can slip through the cracks, leaving organizations vulnerable. That’s where the IT Security To-Do List Checklist in Excel comes in 🔐📊.
This ready-to-use Excel template provides a centralized, organized, and easy-to-manage tool for tracking IT security tasks. Whether you’re updating firewall rules, conducting employee training, or managing compliance deadlines, this checklist ensures accountability, progress visibility, and error-free tracking. Best of all, it’s built in Microsoft Excel—no expensive tools or technical expertise required.
✨ Key Features of IT Security To-Do List Checklist in Excel
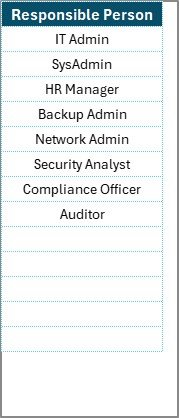
✅ Two Structured Worksheets – Checklist sheet for managing tasks and a List sheet for assigning responsibilities.
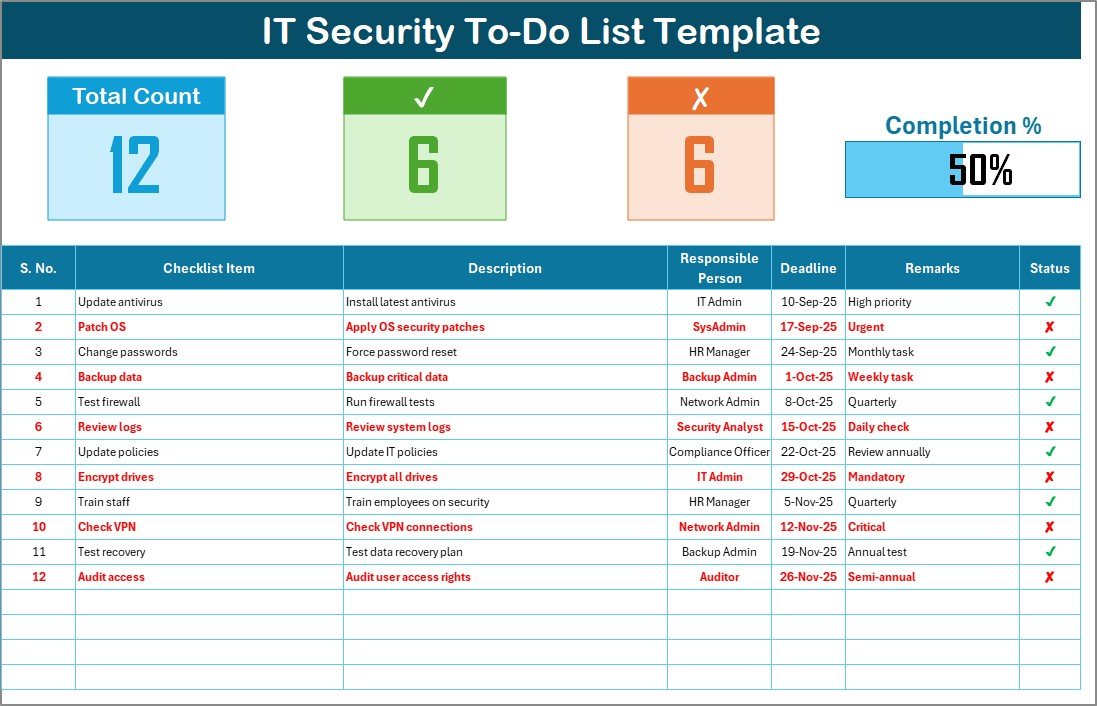
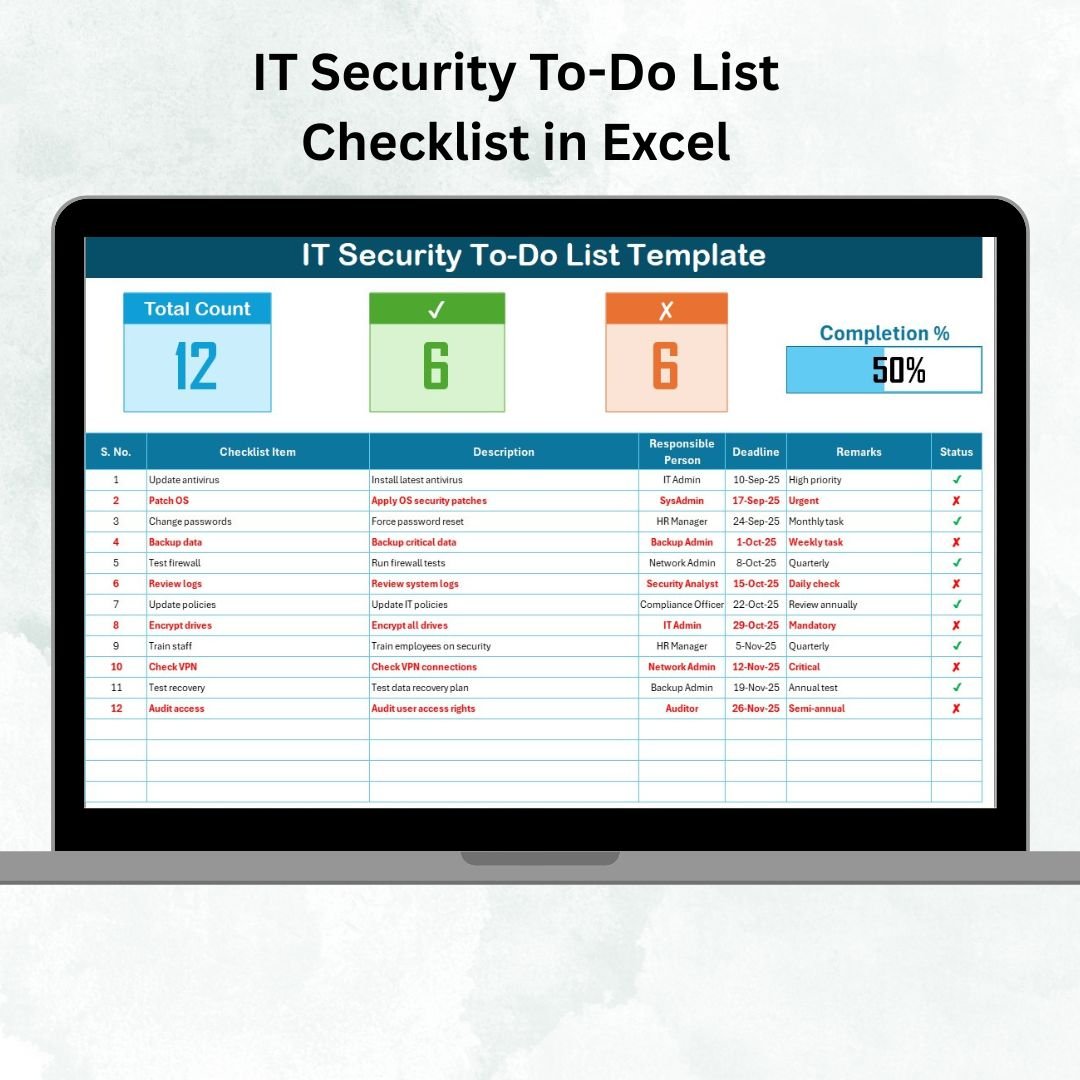
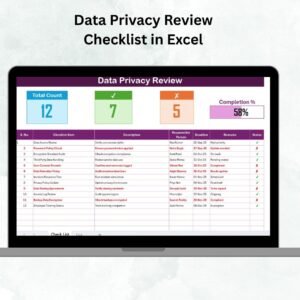
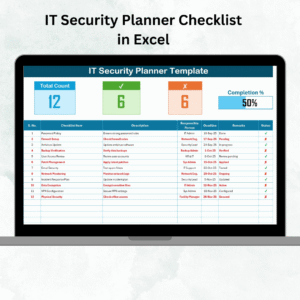
✅ Progress Tracking – Visual progress bar showing total, completed, and pending tasks.
✅ Organized Task Table – Includes Serial No., Checklist Item, Description, Responsible Person, Deadline, Remarks, and Status.
✅ Dropdown Selections – Assign tasks quickly using pre-set lists of responsible persons.
✅ Status Updates – Mark tasks with ✔ for done or ✘ for pending.
✅ Accountability Metrics – Total Count, Checked Count, Crossed Count for instant oversight.
✅ User-Friendly – Designed in Excel, easy to adopt without IT expertise.
✅ Customizable – Add, edit, or remove tasks to fit your organization’s security needs.
✅ Cost-Effective – No extra software required—just Excel.
📊 What’s Inside the IT Security To-Do List Checklist
-
Checklist Sheet – Main working space for recording all security tasks.
-
Summary Section – Shows total tasks, completed tasks, pending tasks, and a dynamic progress bar.
-
Checklist Table – Task details with responsible persons, deadlines, and remarks.
-
List Sheet – Stores the master list of team members, ensuring consistency in task assignment.
🛠️ How to Use the IT Security To-Do List Checklist
1️⃣ Download the Template – Open the Excel file.
2️⃣ Update the List Sheet – Add names of responsible persons.
3️⃣ Enter Security Tasks – Populate the checklist with tasks like patching, backups, or user reviews.
4️⃣ Set Deadlines – Add realistic timelines for completion.
5️⃣ Track Status – Mark ✔ when completed or ✘ when pending.
6️⃣ Review Progress – Use the progress bar for instant updates.
7️⃣ Update Weekly – Keep the checklist fresh to avoid missed tasks.
👥 Who Can Benefit from This IT Security Checklist?
💼 IT Managers – Assign and track security responsibilities.
🛡️ System Administrators – Manage updates, backups, and firewall rules.
📊 Compliance Officers – Prepare audit-ready records.
🏢 Small Businesses – Protect operations without costly tools.
🎓 Educational Institutions – Secure staff and student data.
🏥 Healthcare Providers – Ensure patient data confidentiality.
🏬 Corporate Teams – Strengthen compliance and IT governance.
Click here to read the Detailed blog post
Visit our YouTube channel to learn step-by-step video tutorials
👉 PKAnExcelExpert























Reviews
There are no reviews yet.