In today’s digital-first world, cyber threats are constant and unavoidable. From phishing emails to ransomware, unauthorized access, and data leaks, IT Security Monitoring Checklist in Excel organizations face risks that can disrupt operations and harm reputation. Without a structured monitoring process, even the best firewalls or antivirus tools may not be enough. That’s why the IT Security Monitoring Checklist in Excel is a game-changing solution for businesses of all sizes.
This ready-to-use template empowers IT Security Monitoring Checklist, compliance officers, and managers to stay on top of critical tasks. By centralizing security activities into one simple file, it ensures transparency, accountability, and efficiency—all without expensive software.
✨ Key Features of IT Security Monitoring Checklist in Excel
-
✅ Structured Task Tracking – Capture every security task with details, deadlines, and status.
-
✅ Progress Monitoring – Visual progress bar shows completion percentage in real time.
-
✅ Smart Assignment – Drop-down menus ensure the right person is always accountable.
-
✅ Customizable Template – Add new tasks, fields, or formulas to fit your environment.
-
✅ Audit-Ready Documentation – Generate clear evidence for ISO, GDPR, HIPAA, or PCI DSS compliance.
-
✅ User-Friendly Layout – Works seamlessly in Excel, requiring no technical expertise.
-
✅ Cost-Effective Solution – Get advanced security management without expensive tools.
📦 What’s Inside the IT Security Monitoring Checklist
This template comes with two powerful worksheets:
-
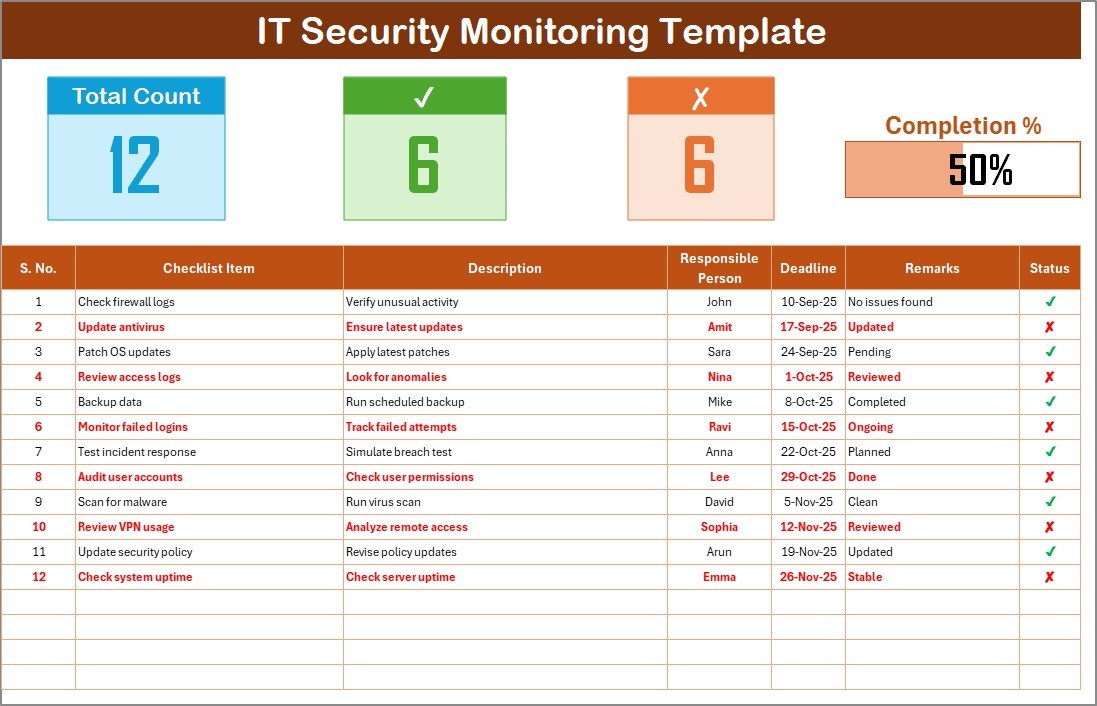
IT Security Monitoring Checklist Sheet
-
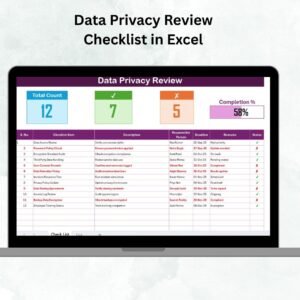
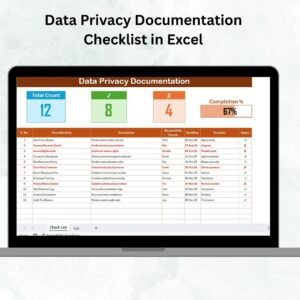
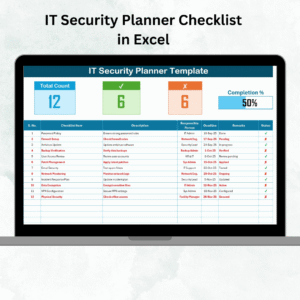
Top section shows task counts, progress bar, and completion metrics.
-
Checklist table includes Serial No., Checklist Item, Description, Responsible Person, Deadline, Remarks, and Status (✔ or ✘).
-
Provides a clear, visual way to track IT tasks such as patch updates, access reviews, or vulnerability scans.
-
-
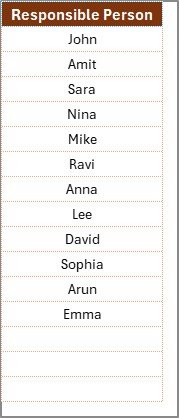
List Sheet
-
Stores a unique list of responsible persons.
-
Linked to the main sheet for easy assignment via drop-down menus.
-
Ensures consistent data entry and prevents duplication errors.
-
🛠️ How to Use the IT Security Monitoring Checklist
-
Open the template and review the default checklist items.
-
Add tasks like “Firewall Audit” or “Data Backup Verification.”
-
Assign responsibility using the drop-down list linked from the List Sheet.
-
Set deadlines to ensure timely action.
-
Update task status with ✔ (done) or ✘ (pending).
-
Track progress with the automatic progress bar.
-
Review weekly to spot overdue or high-risk items.
In just a few steps, your IT monitoring becomes more structured, transparent, and reliable.
👥 Who Can Benefit from This Checklist
-
Small Businesses – Track essential security tasks without investing in complex tools.
-
Healthcare – Ensure compliance with HIPAA by monitoring patient data protection.
-
Finance & Banking – Stay on top of fraud detection, compliance, and customer data security.
-
Education Institutions – Manage student and staff access controls and IT lab security.
-
Corporate Enterprises – Scale IT security across teams and regions while maintaining accountability.
📖 Click here to read the Detailed blog post
🎥 Visit our YouTube channel to learn step-by-step video tutorials























Reviews
There are no reviews yet.